
24x7 Endpoint Detection and Response
Explore Cyber and Data Resilience
- Kroll Responder
- 24/7 Managed SIEM Services
- Kroll Responder MDR for Microsoft Security
- 24x7 Incident Response
- Ransomware Preparedness Assessment
- Threat Exposure and Validation
- Cyber Governance and Strategy
- Incident Response and Litigation Support
- Breach Notification, Call Centers and Monitoring
- Kroll Cyber Partner Program


Imagine being able to detect and respond swiftly to credible threats on your servers, laptops, and workstations backed by the world leaders in cyber investigations and continuous threat hunting and response solutions. Kroll Responder, in an exclusive partnership with Red Canary, gives you that confidence, relieving the burden and impact of cyber threat detection and mitigation on your organization.
Kroll Responder + Red Canary is a powerful combination of technology and people:
- 24x7 monitoring and analysis of endpoints, users, and network activity enhanced with the algorithm- and analyst-driven threat hunting and detection services of Red Canary
- Kroll experts to investigate alerts and assist with any identified threats
Kroll Responder + Red Canary gives you the best of both worlds: Expanded, specialized detection and response capabilities that let your internal information security resources focus on supporting your business.
Managed Detection and Response Delivers Peace of Mind
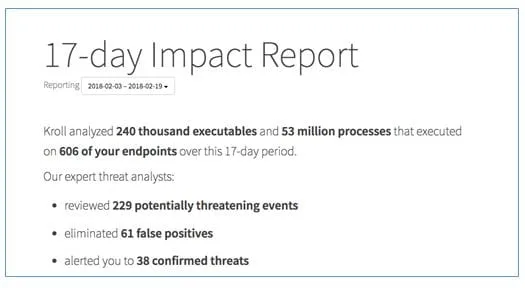
Responder + Red Canary continuously searches for known bad and unusual behaviors, monitoring essentially all endpoint activity:
- All execution events (programs being run, command lines used)
- Metadata modifications (on registry and file system)
- Network connections (connections to the internet and cloud connections)
- Every single unique binary executed across the environment
Our forensic experts – with decades of incident response experience – have seen organizations of all sizes continue to deploy the same automated defenses over and over. The problem? They keep finding themselves breached – often for months or years without detecting it (“dwell time”).
On average, hackers go undetected on financial services networks for more than three months; for retail companies, the dwell time is more than six months. “Attackers Dodge Detection On Retailers’ Networks For Average Of 197 Days: Study.” Securityweek.com. N.p., 2016. Web.
Even larger organizations, with full-time security staff and traditional managed security providers, become so fatigued with daily alert reviews and false positives that they can miss real signs of an intrusion until the damage is done. Plus, internal security teams usually don’t see enough real intrusions to fully recognize dangerous signs and symptoms.
Endpoint Monitoring Enhanced by Behavioral and Forensic Analysis
All collected data is constantly fed through Red Canary’s detection engine in search of malicious or suspicious behavior. Potential threats are then sent to analysts for triage and further analysis.
The detection engine contains multiple threat intelligence sources and IOCs, including Kroll’s learnings from real-world intrusions. Confirmed threats are rated with a severity, classified, and include a timeline of relevant activity. This allows Kroll’s incident responders to immediately begin analysis and remediation for you.

Merging EDR Security and Incident Response
Hunt and Detect
- Red Canary managed endpoint threat detection
-
Behavioral analysis and analytics engine
-
Multiple threat intelligence sources and IOC’s, including Kroll’s learnings from real-world intrusions
-
Analyst-driven threat hunting and identification of threats
-
24x7 expert triage and analysis of potential threats
-
Rapid notification of validated threats
-
24x7 portal access with metrics, reports, and available remediation actions (e.g., block, delete, isolate, ignore)
-
Threat Alerts are shared with the Kroll team
-
Optionally, Kroll team can take active steps to block and contain a threat on your behalf (“Active Response”)
-
Kroll team stands ready to provide deeper forensic analysis, incident response support, and containment advice (no additional engagement required)
Direct Access to Kroll’s Global Cyber Team Expertise
Many of the cyber experts readily available to investigate Responder threat alerts have years of unique experience from their former service with global law enforcement and regulatory agencies:
Federal Bureau of Investigation (FBI)
- Interpol
- U.S. Department of Justice (DOJ)
- Securities & Exchange Commission (SEC)
- U.K. Intelligence and Policing
- Europol
- Hong Kong Police Force
- U.S. Department of Homeland Security
- U.S. Secret Service
- U.S. Attorney’s Office
Kroll Responder MDR for Microsoft Security
Kroll Responder managed detection and response for Microsoft delivers enriched telemetry, frontline threat intelligence and Complete Response capabilities to maximize the value of your native endpoint and cloud technology.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Cyber Threat Intelligence
Threat intelligence are fueled by frontline incident response intel and elite analysts to effectively hunt and respond to threats.
Malware and Advanced Persistent Threat Detection
Our expertise allows us to identify and analyze the scope and intent of advanced persistent threats to launch a targeted and effective response.
Penetration Testing Services
Validate your cyber defenses against real-world threats. Kroll’s world-class penetration testing services bring together front-line threat intelligence, thousands of hours of cyber security assessments completed each year and a team of certified cyber experts — the foundation for our sophisticated and scalable approach.
Data Breach Notification Services
Services include drafting communications, full-service mailing, alternate notifications.
KAPE Quarterly Update - Q4 2023
by Eric Zimmerman

Data Breach Outlook: Finance Surpasses Healthcare as Most Breached Industry in 2023
In 2023 finance was the most breached industry, accounting for 27% of the breaches handled by Kroll, compared to 19% in 2022. Supply-chain risk was a constant menace, driven by the MOVEit Transfer vulnerability and a rise in social engineering. Read more.

CVE-2024-0204: Authentication Bypass Vulnerability in Fortra GoAnywhere MFT
by George Glass

Microsoft Teams Used as Initial Access for DARKGATE Malware
by George Glass, Ryan Hicks

